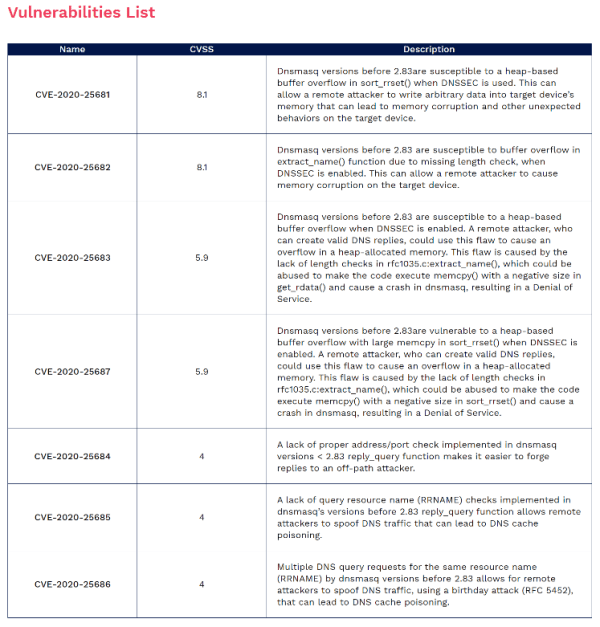
Risk management quantifies and qualitatively describes the risk of Information Security, allowing companies to prioritize risks according to their severity and thus ensure business continuity.
Risk management determines the value of an information asset, identifies the applicable threats and vulnerabilities that exist (or could exist), identifies the existing controls and their effects on the identified risks, determines the potential consequences, and finally prioritizes them.
After this definition, how is it possible to develop a strategy for risk management within a company? What are the main risks associated with Information Security? Also, find out what High Availability and Contingency has to do with risk management and what are their main differences in keeping your system secure.
Keep reading this article and learn how risk management in information security can contribute to your business continuity.
How does Information Security Risk Management work?
Risk management in information security is the process associated with the use of information technology. It involves identifying, assessing, and addressing risks to the confidentiality, integrity, and availability of a company’s assets.
The ultimate goal of this process is to address risks according to a company’s risk tolerance. Companies should not expect to eliminate all risks. Instead, they should seek to identify and achieve an acceptable level of risk for business continuity.
How to develop an Information Security Risk Management strategy?
Managing risks is an ongoing task, and your success will depend on how they are assessed, plans are communicated, and functions are maintained. Identifying the people, processes, and technologies required to help you deal with the steps below will develop a solid foundation for a risk management strategy and program in your company, which can be developed over time.
Identification
This stage is the process of identifying your digital assets that can include a wide variety of information: confidential company information, such as product development and trade secrets; Personal data that can expose employees to cybersecurity risks, such as identity theft regulations. Another example is those companies that handle credit card transactions and need PCI-DSS compliance.
Assessment
This is the process of combining the information you have gathered about assets, vulnerabilities, and controls to define risks. There are many structures and approaches to this.
Treatment
Once a risk has been assessed and analyzed, the company will need to select the risk treatment options. In this scenario, companies can accept the risk or prevent it.
Communication
Regardless of how risk is handled, the decision needs to be communicated within the company. Stakeholders need to understand the costs of whether or not to address risk and the reason behind such a decision. Responsibility and accountability need to be clearly defined and associated with individuals and teams in the company to ensure that the right people are engaged at the right times in the process.
Main risks associated with Information Security
Security risks are inevitable, so the ability to understand and manage risks for systems and data is essential to a company’s success.
If you are able to address the risks below and respond effectively to security incidents, you can find out how to better resist cyber threats and reduce potential risks in the future.
Privilege Abuse
In most technology environments, the principle of least privilege is not valid. There are many reasons why privileges greater than necessary have been granted to a user.
Granting excessive permissions is problematic for two reasons: approximately 80% of attacks on corporate data are actually performed by active or dismissed employees. Privileges excessively granted or not revoked at the right time make it simple for someone to perform malicious actions.
Third-party Access
A number of third parties, including suppliers, contractors, consultants, and service providers have access to network resources, which allows them to modify, replace, or impact your company’s operational service. This access is considered privileged and needs to be even more protected than the access by an employee.
Companies apply efforts to protect their networks, but forget about third-party access security controls. These controls can protect third-party access to privileged credentials, as well as strengthen security aspects that are normally exploited by attackers to gain access to the corporate network.
Insider Threats
When it comes to data breaches, employees themselves can be one of the biggest risks to an organization. These threats can be: accidental, when personnel is only poorly trained; negligent, when employees try to bypass implemented policies; or malicious (the most dangerous), when an employee is motivated by financial gains, espionage, or revenge.
HA (High Availability) and DR (Disaster Recovery / Contingency) as metrics for Risk Management
Any good system these days must be built to expect the unexpected. No system is perfect and, at some point, something will happen that will cause a system to malfunction (a fire, a hurricane, an earthquake, human error – the list goes on). Since systems can fail in different ways, they need to be designed with the expectation that a failure will occur.
Thus, there are two related, but generally confusing, topics that work on the system architecture that mitigate failures: high availability (HA) and disaster recovery (DR).
High availability simply eliminates single points of failure, and disaster recovery is the process of putting a system back into an operational state when it goes down. In essence, disaster recovery is triggered when high availability fails.
Fundamentally, high availability and disaster recovery have the same goal: to keep systems up and running in an operational state. The main difference is that high availability is designed to deal with problems when a system is running, while disaster recovery must deal with problems after a system failure.
Regardless of a system’s high availability, any system in production, no matter how trivial, needs to have some kind of disaster recovery plan in place. And this should be included in your information security risk management strategy.
About Version 2
Version 2 is one of the most dynamic IT companies in Asia. The company develops and distributes IT products for Internet and IP-based networks, including communication systems, Internet software, security, network, and media products. Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About Senhasegura
Senhasegura strive to ensure the sovereignty of companies over actions and privileged information. To this end, we work against data theft through traceability of administrator actions on networks, servers, databases and a multitude of devices. In addition, we pursue compliance with auditing requirements and the most demanding standards, including PCI DSS, Sarbanes-Oxley, ISO 27001 and HIPAA.