Intro
In this article we will look further into some of the options that Nmap offers. Since we have looked into the Null, Xmas, and FIN scans, we will continue down this path of port scanning techniques, and for this article we will focus on ACK Scan (-sA), Window Scan (-sW), and Maimon Scan (-sM).
After the Scans section, we will quickly review some other things that might be worth considering, which I felt were an important inclusion.
Before we dive any further into our topic, I would like to use this opportunity to emphasize (again) how our understanding of the system(s) we are looking to scan, and its scope, is one of the most vital things for successfully tackling whatever job we were brought to do.
One (rather crude) example would be if our job was to scan the whole Internet. First question that should come to mind is – Can I use Nmap for this? Should I?
The answer here is simple – yes, you most definitely can! Should you? Well… no, you should not use Nmap to scan the whole Internet. You should use Masscan, for example. (There are caveats here, of course – but this goes beyond the scope of our article)
Without further ado, let’s get to it!
Scans
- TCP ACK Scan (-sA)
- TCP Window Scan (-sW)
- TCP Maimon Scan (-sM)
Examples, command-line flags, scripts, options
- Timing Templates (-T)
- IPv6 Scanning (-6)
- Selecting Ports to Scan
TCP ACK Scan (-sA)
TCP ACK Scan is generally used to investigate firewalls, more precisely – their rules; this is how it discerns if the Firewalls are stateless or stateful, and which ports are the ones that are filtered. The only flag set in this scan is the ACK flag. It is important to note that the ACK Scan never ‘knows’ open or open | filtered ports.
Unfiltered systems will be returning an RST packet on both open and closed ports. In turn, Nmap would then label them as unfiltered – since the ACK packet was able to reach it. However, we can’t know (only from this) if they are indeed open or closed.
Ports that send ICMP error and/or not respond would be considered (and tagged) as filtered.
ACK Scan is invoked with the -sA option added to your command.
Summing up:
- If there’s no response received – the assigned state is filtered
- If we get an ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) – the assigned state is filtered
- If a probe response is a TCP RST packet – the assigned state is unfiltered
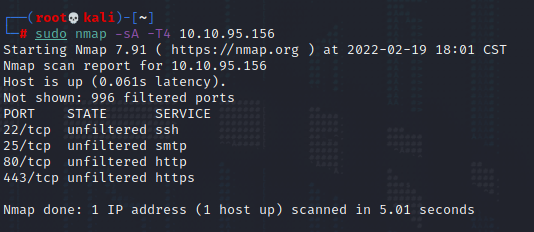
Example ACK scan – we know these ports are open since its our test machine – but note that this result is not enough to infer that (if we don’t have the knowledge of the system
TCP Window Scan (-sW)
The Window Scan – which we can invoke by adding -sW to our command – has the same mechanism as the ACK scan, but, rather than checking if the RST packet is returned, it looks to se the TCP Window Value of the returning RST packet. The big difference here is the fact that the Window Scan can discern if the port is open or closed, rather than just checking if it is (un)filtered. The flag sent is a sole ACK flag, same as in the ACK Scan.
Note that a system with no firewall won’t give us enough (if any) information – in contrast to the ACK scan. But, if we were to scan a server that’s behind a firewall, the whole story changes and we get much better results – also, remember that if we get a result showing the ports are closed (image below) this can actually mean that these are open. (Again, in contrast to the ACK scan, that would label these ports as unfiltered)
One should also keep in mind that this scan might not work on the majority of the systems found out there on the Internet, due to the fact that it leverages a rather niche implementation detail – which many systems might not support, or just care for.
Summing up:
- If the response is ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) – the assigned state is filtered
- If no response is received – the assigned state is filtered
- If we get a TCP RST response with a zero window field – the assigned state is closed
- If we get a TCP RST response with a non-zero window field – the assigned state is open

Example Window Scan on our test machine showing 4 closed ports (which we know are actually open) so we know the firewall is not blocking them
TCP Maimon Scan (-sM)
The Maimon Scan, named after Uriel Maimon who first showed this scan in 1996, sets two flags – FIN and ACK. In response, we should receive an RST packet – whatever state the port may be in – from RFC 793 – TCP. Here, Uriel observed that many BSD-based systems would just drop the packet, if the port in question was open.
However, this scan might not work on most systems today, since they usually just send a RST packet back for all of the ports, thus showing every port to be closed – failing our scan attempts.
Summing up:
- If the response is ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13) – the assigned state is filtered
- If no response is received – the assigned state is open | filtered
- If we get a TCP RST packet in response – the assigned state is closed
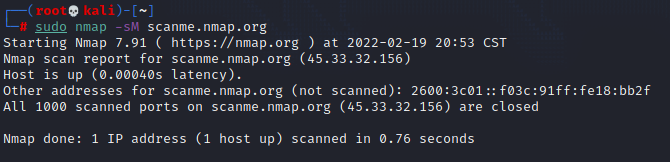
Example of a failed Maimon Scan
Examples, command-line flags, scripts, options
Timing Templates (-T)
You can fine tune your timing controls with Nmap, however, as powerful as it is, this introduces much more complexity. Luckily, Nmap also offers something much more simple with its six timing templates. They are used by adding a number (0-5) to your -T option -T0, -T1, etc.
Timing templates and their effects are given below (from the Nmap official book/website)
|
T0 |
T1
|
T2
|
T3
|
T4
|
T5
|
| Name |
Paranoid |
Sneaky |
Polite |
Normal |
Aggressive |
Insane |
| min-rtt-timeout |
100 |
100 |
100 |
100 |
100 |
50 |
| max-rtt-timeout |
300000 |
15000 |
10000 |
10000 |
1250 |
300 |
| initial-rtt-timeout |
300000 |
15000 |
1000 |
1000 |
500 |
250 |
| max-retries |
10 |
10 |
10 |
10 |
6 |
2 |
| initial (and minimum) scan delay (–scan-delay) |
300000 |
15000 |
400 |
0 |
0 |
0 |
| maximum TCP scan delay |
300000 |
15000 |
1000 |
1000 |
10 |
5 |
| maximum UDP scan delay |
300000 |
15000 |
1000 |
1000 |
1000 |
1000 |
| host-timeout |
0 |
0 |
0 |
0 |
0 |
900000 |
| min-parallelism |
Dynamic, not affected by timing templates |
|
max-parallelism |
1 |
1 |
1 |
Dynamic |
Dynamic |
Dynamic |
| min-hostgroup |
Dynamic, not affected by timing templates |
| max-hostgroup |
Dynamic, not affected by timing templates |
| min-rate |
No minimum rate limit |
| max-rate |
No maximum rate limit |
| defeat-rst-ratelimit |
Not enabled by default |
Source
IPv6 Scanning (-6)
Nmap also supports IPv6, at least for most important options. Version detection, ping scanning (TCP-only), connect scanning, are all supported. Since the addresses are IPv6, that means hexadecimal, so an address might look like this – 2001:0db8:85a3:0000:0000:8a2e:0370:7334. Luckily, hostnames are accepted too. You and your target both need to be configured for IPv6, in order to use IPv6 option in Nmap.
Since you’re most likely not using IPv6, don’t worry, there are many free IPv6 tunnel brokers out there.
Selecting Ports to Scan
If no other ports are specified, Nmap will scan 1000 most popular ports – for each protocol that it is scanning. However, you can also specify the ports you wish to scan manually. Let’s look at some examples.
-p 80 (scan a single port, in this case port 80)
-p ssh (you can use port name too, instead of port numbers)
-p 22, 80, 445 (you can scan more than one port, by separating them with a comma)
-p80-85, 139, 5000-5010 (you can specify port ranges by separating them with a hyphen. Multiple port ranges can be specified by separating them with a comma)
-p-200, 5000- (when you omit the beginning of a range, Nmap will start from port one, similarly, if you end with a hyphen it will scan all remaining ports up to → 65535. This scan would scan all ports from port 1 to port 200, then from port 5000 to port 65535
-p- (you can scan the whole range, if you omit beginning and end numbers)
-p 1-1023, [1024-] (you can also use square brackets to encase a range, so that Nmap only scans those if they are registered within nmap-services. Here, we would scan the first 1023 ports, and we would also scan all the remaining ports that are registered in nmap-services.
Conclusion
We’ve again gone over quite a bit, yet probably opened up even more questions than before. As you might be aware, Nmap offers a plethora of options – from host discovery, OS and version detection – to port scanning and IP protocol scanning. There’s also a whole topic – and a quite big one at that – on the NSE – Nmap Scripting Engine, that we will hopefully cover in some of our upcoming articles in this series.
Finally, I would like to again remind you to add sudo before your Nmap commands, to leverage its power fully, since raw socket / packet privileges require you to have root access. Also, by default, a privileged user runs a stealth (-sS – TCP SYN) scan – which is faster and stealthier!
Resources used:
Nmap: the Network Mapper – Free Security Scanner
Nmap Network Scanning – Gordon “Fyodor” Lyon




