Pandora FMS is a proactive, advanced, flexible and easy-to-configure monitoring tool according to each business. Pandora FMS integrates with the needs of the business, being able to monitor servers, network equipment, terminals and whatever is necessary.
In this article we will focus on monitoring using Pandora FMS, bearing in mind the new reality, which has arrived to stay, known as “Digital Transformation”.
Digital Transformation
First of all, let’s start by understanding what Digital Transformation is all about, a widely used term, but at the same time somewhat confusing for many people, due to its broad definition.
Digital transformation is a concept that encompasses the integration of the different technologies, used in the different areas of a company, fundamentally changing the way it works and delivers value to its customers. It is also a cultural shift that requires organizations to constantly challenge the status quo, experiment, and feel comfortable with the change.
It is not new that technology advances faster and faster generating a constant challenge, that is why we must be on the watch for these advances, to be able to adopt new technologies and achieve the cycle of “Continuous Improvement”, taking advantage of the tools that allow us to be more and more efficient.
As part of this change, there are key technologies that allow us to digitize our information and adapt to this new reality that is here to stay.
- Cloud Computing (Amazon AWS, Microsoft Azure, Google Cloud): It gives your organization faster access to the software it needs, new features and updates, as well as data storage. Cloud computing allows you to be agile enough to transform quickly.
- Information technology: It allows an organization to focus its investment on talent, research and development, and customized solutions that support the requirements and processes that differentiate it in the market.
- Machine learning and artificial intelligence technologies: They provide organizations with more accurate information for decision-making on sales, marketing, product development and other strategic areas.
- Other technologies that drive business transformation are: blockchain, blockchain, augmented reality and virtual reality, social networks, and the Internet of Things (IoT).
Since the beginning of computing, companies had at least one server/computer as part of their daily tasks. This implied additional tasks such as: technical support, and infrastructure maintenance.
Some years ago, it was common to find email servers, installed in the company, generating the great challenge to keep a critical service, like this one, running 24/7. Today there are private cloud solutions such as: Microsoft 365 or Google Apps, that allow you to have email with a very high SLA, without the need for your own infrastructure, using the service as SAAS (Software as a Service).
To understand where we are at and where to start, with the digital transformation process, we are going to explain the four most common infrastructure scenarios:

On-Premise (Local Infrastructure): Servers that work in the company and require a great effort to maintain them.
IaS Cloud (Infrastructure as a Service): In this scenario, virtual machines can be run in the cloud, such as, for example, a Windows Server, some Linux distribution where you install the essential tools to use the corporate application that you need to use. The provider ensures the availability of the virtual machine and the company is responsible for the software that is installed. In this case, Amazon AWS, Microsoft Azure, Google Cloud, etc. can be used.
PaaS Cloud (Platform as a Service): Services that work in the cloud and that have a platform such as: SQL Server, Oracle, SAP, Docker, Etc.
SaaS Cloud (Software as a Service): Services that work in the cloud and have a management tool, such as Exchange Online, Google Apps (Corporate Gmail), OneDrive, Google Docs, Etc.
After this introduction, we are going to understand the value of Pandora FMS for any of the previous scenarios, at the time of Digital Transformation.
Some time ago, we already published an article on this blog with the installation script for IaS Cloud. As a requirement you need to have a Virtual Machine with CentOS 7, which has 2 GB of RAM and 20 GB of Disk.
Executing the following command: curl -Ls https://pfms.me/deploy-pandora | sh on a computer that has an Internet connection, you will obtain an installation of Pandora FMS Community in an On-Premise scenario or in the cloud that you use:
https://pandorafms.com/community/get-started/
For the Enterprise version, we have a Free 30-day Trial.
Now that you know that you can install Pandora FMS in the scenario that is most convenient for you, we are going to see which are the required ports to be able to use the tool from a public cloud:
| Port | Description |
| 443 TCP (https) | WEB console |
| 41121 TCP (Tentacle) | Software Agent Connection/td> |
With this configuration you can use Pandora FMS key features. We are going to see just a few of them. Very useful for this reality of continuous changes.
Remote Configuration, Policies and Collections: With this configuration you can make all the changes on the monitoring agents, using Pandora FMS web console, being able to build the Agent Plugins and distributing them in a centralized and simple way.

Agents with Remote Configuration
Satellite Server: A very interesting possibility is to set up an agent with advanced features. It allows you to discover the different remote networks, servers, and network computers, using ICMP, SNMP and WMI protocols. It is not necessary to open any ports on the firewall, where the Satellite Server is installed. You have the possibility of reaching Pandora FMS server with port 41121 TCP Tentacle and, for example, remotely monitor the devices from the different locations and/or branches.
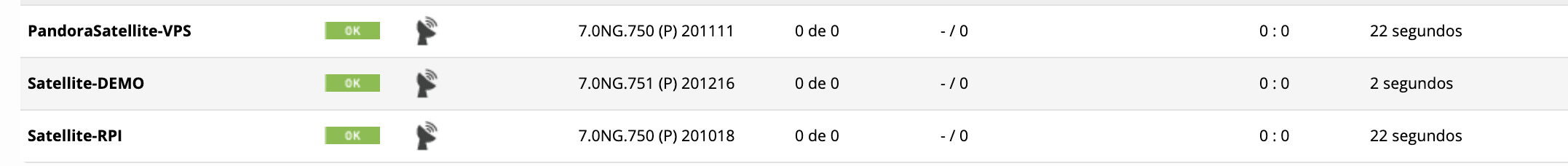 Several Satellite Servers, reporting to a console in Azure
Several Satellite Servers, reporting to a console in Azure


Ubiquiti AP UC-AC-LR (Satellite through SNMP)

Pandora FMS Ubiquiti AP UC-AC-LR Web Console
https://pandorafms.com/docs/index.php?title=Pandora:Documentation_es:Arquitectura#Servidor_Sat.C3.A9lite
Finally, and as a complementary tool, you can count on the possibility of having usage and consumption metrics in the cloud, from the “Discovery” option, or with add-ons from the Enterprise library.

Discovery Cloud View
At the time I wrote this article, the clouds supported by Pandora FMS were:

*It is possible that new cloud technologies will be added over time.
In the next tree view you can see some of the metrics that we have available for AWS and Azure. In this view, you can see the status of the virtual machines, the consumption of Network, Memory, etc.
All these parameters are configured according to the specific needs of each client.

https://pandorafms.com/docs/index.php?title=Pandora:Documentation_en:Discovery#Discovery_Cloud (Discovery Cloud Documentation)
Finally, Microsoft 365 cloud has an API to be able to monitor the health status of its services. Pandora FMS has a plugin in the Enterprise library that allows you to collect data from the Microsoft 365 API.
https://pandorafms.com/library/pandora-office-365-monitoring/
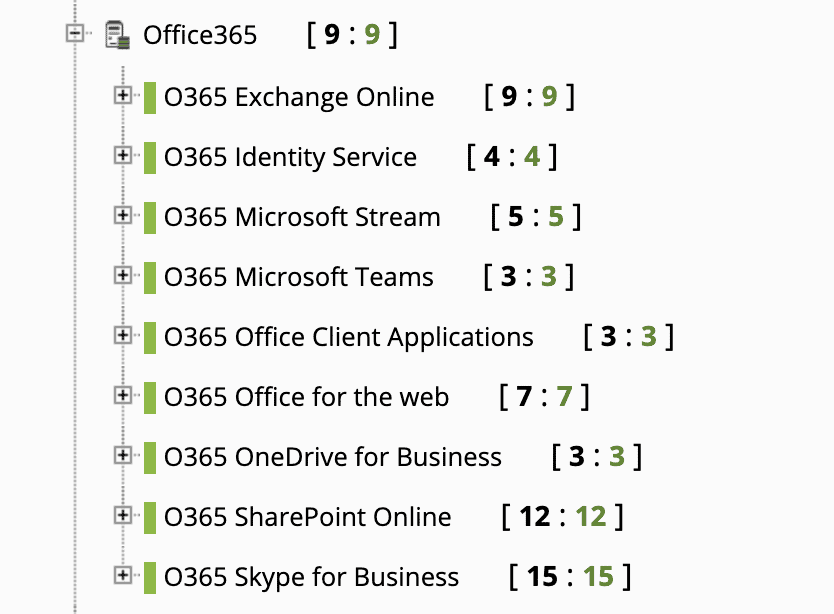
Partial View of Microsoft 365 Services
I hope this article was useful for you to understand what the best monitoring scenario for your company is.















 Several Satellite Servers, reporting to a console in Azure
Several Satellite Servers, reporting to a console in Azure








