Intro
Continuing where I left off, I will look at some more tools you can use to look at the Registry of your Windows host, as well as some useful keys.
Tooling
I am sure there are many tools out there, created specifically for this purpose, and please feel free to search for them. I will cover the ones that I’ve used or know.
From previous parts, you know that the Registry Editor works only with live systems and can’t load exported hives, so keep that in the back of your mind.
When you need that offline functionality, you can use some of the following tools.
Zimmerman’s Registry Explorer
The author of this tool has created a bunch of tools that can be extremely handy for performing Digital Forensics. (Check out the stuff here)
One of those tools is his Registry Explorer. Registry Explorer has the ability to load multiple hives at the same time, while it can also use/add data from the transaction logs into the hive, enriching it with more accurate data. It also has the Bookmarks functionality which will contain forensically valuable keys. You can use the bookmarks to immediately pull up some interesting keys and/or values.
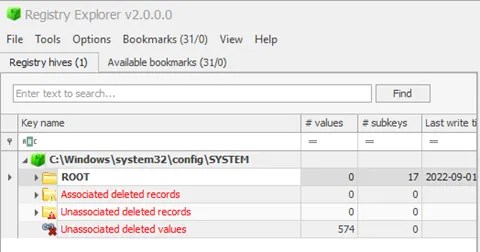
Above, I just loaded one hive (SYSTEM) from my live system, and I already have 31 recommendations (bookmarks) from Registry Explorer. As a very simple demo, when I switch over to that tab, I can immediately glean some interesting information. For example, I can immediately pick up the hostname of the device.

I filtered out the bookmarks here, showing only the Device Name. As you can see, you even have a small window below with the category, name, path, and description of the key.
On the righthand side of this view, I can see my hostname.
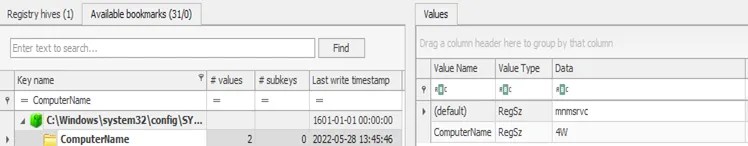
Under Data, I can see the name of my device – 4w.
I will circle back to the Registry Explorer, but let me briefly introduce another tool, for the sake of your awareness.
RegRipper
A useful utility that can take the have as input and spit out a report which will try to extract data from (forensically) important keys/values within that specific hive. However, note that RegRipper doesn’t take transaction logs into consideration, which is also stated it in the repo’s readme file:
This tool does NOT automatically process hive transaction logs. If you need to incorporate data from hive transaction logs into your analysis, consider merging the data via Maxim Suhanov’s yarp + registryFlush.py, or via Eric Zimmerman’s rla.exe which is included in Eric’s Registry Explorer/RECmd.
Luckily, you can use the Registry Explorer for this.
SYSTEM – Registry Explorer

As you can see, Registry Explorer will even give you the ControlSet – Control Set is basically the hive that keeps the device configuration data that’s used for the control of the system startup.
From the image above, Registry Explorer apparently has some knowledge about the USB devices I’ve been plugging in these days…
Let’s check it out.

The first USB device on the list is an external DVD/Optical drive that I plugged in to transfer some stuff from a CD. (don’t @ me please, they still have some uses 😊)
And, as you can see, I’ve also plugged in four different USB devices, two of them being Kingston made flash drives. All with the timestamps, etc. (I really did this, as I was transferring/cleaning up some old stuff.)
All this goes to show how simple and useful the Bookmarks option that Registry Explorer has can be.
Specific Registry Keys
Here, I’d like to mention some specific keys/values that might be of interest to you. This can pertain to system, recently used apps, or even a user. That doesn’t matter.
OS Version
For the OS version, I just view the SOFTWARE\Microsoft\Windows NT\CurrentVersion key.
From Registry Explorer, one could ascertain that the device I’m doing this demo from is running Windows 11 Pro.

Current Control Set
As I mentioned before, this hive will have the device config data that is used for the control of the system startup. There are (usually) two sets – ControlSet001 and ControlSet002, within the SYSTEM hive.
Generally, ControlSet001 points to the Control Set your device used to boot. ControlSet002 will be what’s known as last known good config.
They can be found at SYSTEM\ControlSet001 and SYSTEM\ControlSet002.
Do note that there’s also a volatile Control Set, created by Windows, when the device is live, and it’s called CurrentControlSet – location: HKLM\SYSTEM\CurrentControlSet.

This is an important hive, and the one you will probably end up referring to for the most part of your investigation.
In the screenshot above I checked the SYSTEM\Select and within I’ve found the last known good entry which tells me that the ControlSet001 holds the last known good config.
SYSTEM\Select\LastKnownGood – key that will hold the last known good config, regarding the Control Sets.
Computer Name
This one is always important during the investigation, and you will look it up by checking the
SYSTEM\CurrentControlSet\Control\ComputerName\ComputerName
From Registry Explorer. On the righthand side of the app, you’ll see the keys and their values/data.
Timezone Information
This one is usually used to figure out the time zone of the device i.e., where it is located. It can help you figure out that timeline of events, which is of great importance to you – the investigator!
You would want to start here:
SYSTEM\CurrentControlSet\Control\TimeZoneInformation
Devices
This is all about tracking the USB devices that were plugged into the system. It will usually contain the vendor id, version of the USB device, and product id. This is cool as it can help you to identify devices themselves. These locations will also store timestamps for the devices that were plugged in.
SYSTEM\CurrentControlSet\Enum\USBSTOR
SYSTEM\CurrentControlSet\Enum\USB
(I already added this screenshot above, where I mentioned the USB I recently plugged in)
It’s also important to know when this USB was plugged in for the first and last time, and you can find that out by checking the
SYSTEM\<CurrentControlSet>\Enum\USBSTOR\<vendor_prod_version>\<serial>\Properties\<some_GUID>\<value>The values you are interested in are – 0064, 0066, and 0067. 64 is the first connection time, 66 last connection time, and 67 the last removal time.
It would look something like this:

And, on the right hand side, I can see the timestamp associated with my Kingston USB that I’ve used.
For 0067 – when I removed the USB device:

It was on 28th of August, at 17:05. (Which I know is true)

Note that Registry Explorer already parses this data, and you can get it if you select the USBSTOR key.
USB Name
The name of the plugged in USB can be found here:
SOFTWARE\Microsoft\Windows Portable Devices\Devices

Under data, an investigator would figure out that the USB I used to be named – GADFLY.
Conclusion
And there you have it! More registry stuff. I’ve been focusing a bit more on the tooling, as it can really save you a lot of time and trouble. But, I will (sometime in the near future) also make a ‘compilation’ of sorts, regarding more of these interesting keys. Even though I covered some here, there’s a lot more stuff that will be of interest to an investigator.
Stay tuned!
Cover image by Immo Wegmann
#registry_forensics #windows #registry_explorer #regripper
About Version 2 Digital
Version 2 Digital is one of the most dynamic IT companies in Asia. The company distributes a wide range of IT products across various areas including cyber security, cloud, data protection, end points, infrastructures, system monitoring, storage, networking, business productivity and communication products.
Through an extensive network of channels, point of sales, resellers, and partnership companies, Version 2 offers quality products and services which are highly acclaimed in the market. Its customers cover a wide spectrum which include Global 1000 enterprises, regional listed companies, different vertical industries, public utilities, Government, a vast number of successful SMEs, and consumers in various Asian cities.
About VRX
VRX is a consolidated vulnerability management platform that protects assets in real time. Its rich, integrated features efficiently pinpoint and remediate the largest risks to your cyber infrastructure. Resolve the most pressing threats with efficient automation features and precise contextual analysis.
















